| Multifunctional |
| v-ENGINE is a Vigilate product designed to manage IP cameras with video recording and video analysis functions which, in real time, can trigger alarm events. Thanks to a suite of protocols, v-ENGINE is also able to interface and integrate a series of other systems from the main brands in the sector such as: access control, fire prevention and anti-intrusion. Its functions are all-in-one as follows:
- NVR
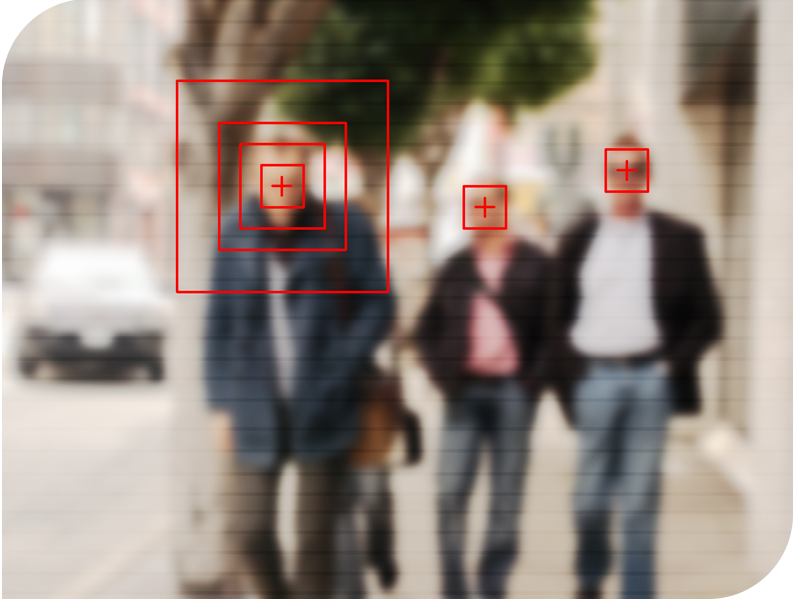
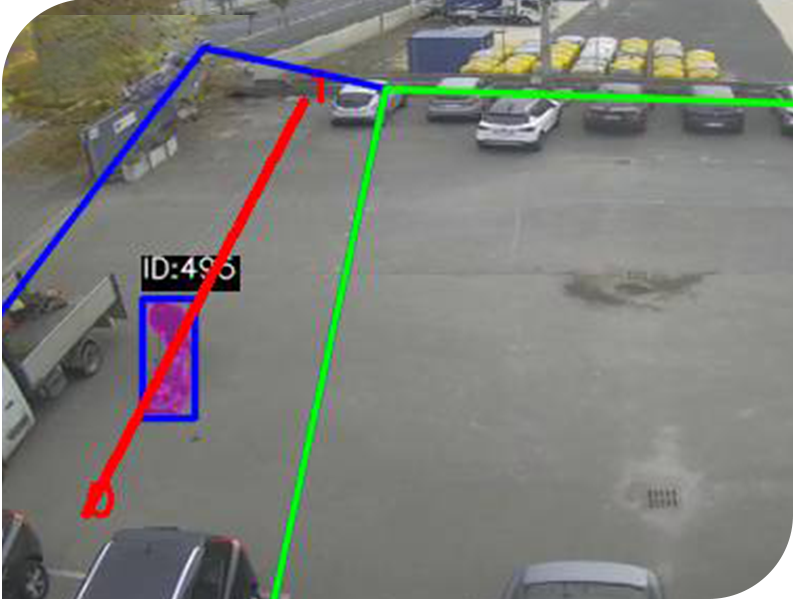
- Neural Video Analytics
- Integration of third party systems
- Gateway to the supervisor |
| Performance |
| v-ENGINE allows you to operate video analysis algorithms simultaneously on all connected cameras, ensuring the processing of 8 images per second at VGA or CIF resolution for each camera. v-ENGINE allows on-board recording of all the video streams of the connected cameras at the maximum resolution of the camera up to a max of 8Mpx. |
| Data security |
| Data and images are stored in an encrypted manner directly in the product as well as being sent to the v-SUITE Xentinel control system. The video streams sent are authenticated. |
| Configuration and integration |
| It is possible to configure v-ENGINE via a web configurator from any remote location via the on-board web server. It represents on the building where a single manager of all security devices is installed, directly managing the balanced sensors of traditional anti-intrusion systems and existing cameras. Furthermore, it also integrates other security systems such as access control units and fire and smoke detection systems. Towards the v-ENGINE platform it is natively integrated with the v-SUITE VIGILATE Xentinel supervisor, but has the SDKs necessary to integrate with the main market platforms such as Milestone, Genetec, Axxonsoft. |
Please note that the technical data, information and images contained in this document are for reference only.
Vigilate S.r.l. reserves the right to change the data, drawings and information here at any time and without notice contained.
All trademarks belong to their respective owners; third-party trademarks, logos, product names,
trade names, corporate and company names mentioned are trademarks owned by their respective owners or
registered trademarks of other companies and have been used for explanatory purposes only, without any
intent to violate the Copyright rights.